Market Overview
The USA Identity and Access Management market is valued at USD 7.36 Billion in 2025 with an approximated compound annual growth rate (CAGR) of 15.53% from 2024-2030, based on a five-year historical analysis. The market is primarily driven by the increasing threats of cybersecurity breaches and the need for regulatory compliance in various industries. Organizations are investing significantly in IAM solutions to manage user identities, protect sensitive data, and ensure compliance with regulations such as GDPR and HIPAA.
Cities such as San Francisco, New York, and Washington, D.C. dominate the Identity and Access Management market due to their robust technology ecosystems and high concentration of enterprises across various sectors, including finance, healthcare, and government. The presence of leading technology companies and startups, along with a skilled workforce in these urban centers, fosters innovation and growth within the IAM space. Furthermore, government agencies and large corporations in these cities prioritize IAM to safeguard against rising cyber threats.
The implementation of stringent data protection laws is a critical driver for the Identity and Access Management market. In 2022, approximately 78% of organizations reported adjusting their IAM practices to comply with regulations, including the California Consumer Privacy Act (CCPA) and the General Data Protection Regulation (GDPR). These laws impose heavy penalties for data breaches and non-compliance, pushing organizations to fortify their IAM practices.
Market Segmentation
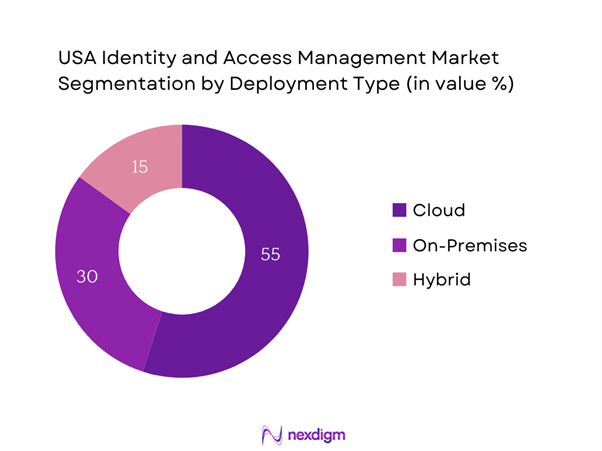
By Deployment Type
The USA Identity and Access Management market is segmented by deployment type into cloud, on-premises, and hybrid solutions. The cloud segment has recently emerged as the dominant segment, reflecting an ongoing trend towards cloud adoption among organizations. This preference is largely due to the flexibility and scalability that cloud solutions offer compared to traditional on-premises systems. The increasing need for remote access solutions, coupled with the lower upfront costs associated with cloud deployments, has further accelerated this transition. Moreover, cloud-based IAM solutions allow for easier integration with mobile devices and other contemporary technologies, enhancing usability for firms aiming to adapt to evolving business landscapes.
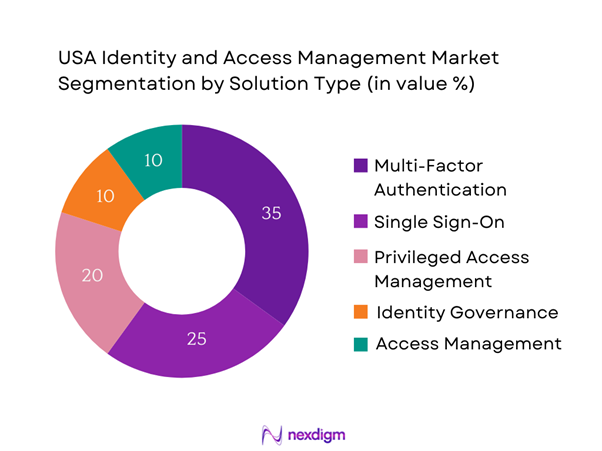
By Solution Type
The market is also segmented by solution type, including multi-factor authentication, single sign-on, privileged access management, identity governance, and access management. Multi-factor authentication services hold a significant share of the market due to their essential role in safeguarding sensitive information against unauthorized access. The increasing occurrence of data breaches has heightened organizational emphasis on implementing advanced security measures, which has led to widespread adoption of multi-factor authentication solutions. These services add an additional layer of security by requiring multiple forms of verification, thereby effectively reducing the risk of identity theft and improving overall user confidence.
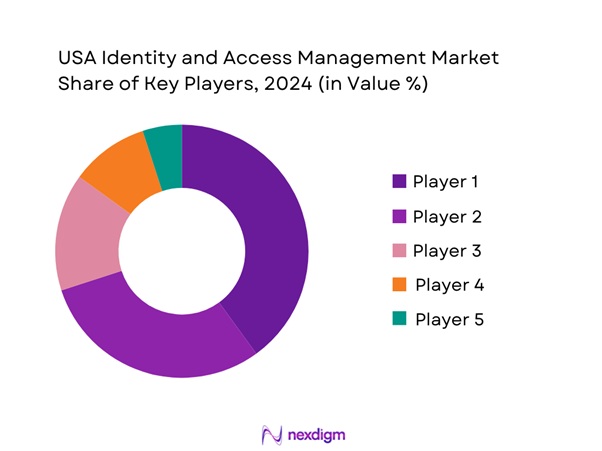
Competitive Landscape
The USA Identity and Access Management market is dominated by a few major players, including global technology giants like Microsoft, IBM, and Okta, which have established strong market positions due to their comprehensive product offerings and significant R&D investments. This consolidation highlights the substantial influence of these key companies in shaping market trends and driving innovation in IAM solutions.
| Company | Establishment Year | Headquarters | Product Offerings | Market Approach | Key Innovations |
| Microsoft | 1975 | Redmond, WA | – | – | – |
| IBM | 1911 | Armonk, NY | – | – | – |
| Okta | 2009 | San Francisco, CA | – | – | – |
| Ping Identity | 2002 | Denver, CO | – | – | – |
| CyberArk | 1999 | Petah Tikva, Israel | – | – | – |
USA Identity and Access Management Market Analysis
Growth Drivers
Increasing Cybersecurity Threats
In recent years, the U.S. has experienced a significant increase in cybersecurity threats, with the FBI reporting over 1.4 million incidents of cybercrime in 2022, causing estimated losses of USD 10.3 billion. This alarming trend has prompted organizations across various sectors to prioritize security measures. According to Cybersecurity & Infrastructure Security Agency (CISA), 75% of organizations highlighted that they increased their cybersecurity budgets in response to chilling incidents, specifically targeting identity-related breaches which emphasize the need for robust IAM solutions.
Regulatory Compliance Requirements
With a rapidly evolving regulatory landscape, companies in the U.S. face stringent compliance requirements from laws and regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). As of 2023, nearly 36% of companies were cited for non-compliance issues related to identity management. The average penalty for privacy violations linked to IAM systems is estimated at USD 1.5 million, which has compelled organizations to enhance their compliance strategies through effective IAM solutions to avoid such financial ramifications.
Market Challenges
High Implementation Costs
The high costs associated with implementing robust Identity and Access Management systems pose a significant challenge for many organizations. Many businesses struggle to justify these expenditures, often citing budget constraints and the need for additional resources to integrate IAM solutions seamlessly into existing systems. This financial barrier limits the adoption of IAM solutions, particularly for small to medium-sized enterprises with tighter budgets.
Complex Integration with Legacy Systems
Integrating modern identity management solutions with existing legacy systems often poses technical challenges for organizations. Many U.S. companies, particularly in finance and healthcare, rely on legacy infrastructure that may not support modern IAM functionalities. The complexities surrounding such integrations have led to hesitancy among organizations to adopt comprehensive IAM solutions that are critical to addressing current security challenges.
Opportunities
Rising Demand for BYOD Policies
The rise of Bring Your Own Device (BYOD) policies in the workplace has created a pressing need for specialized Identity and Access Management solutions. A survey found that 70% of businesses implemented BYOD policies as a strategy to improve employee productivity and satisfaction in recent years. As more employees use personal devices to access corporate resources, the necessity for robust IAM solutions to secure these access points has surged. With the total number of mobile devices expected to reach 24 billion by end of 2025, organizations will need to invest more significantly in IAM solutions to manage identities and secure access effectively.
Emerging Technologies
Emerging technologies such as artificial intelligence (AI) and biometrics present considerable growth opportunities within the IAM market. Furthermore, the biometric segment, including facial recognition and fingerprint scanning, is projected to witness rapid expansion, with the number of companies adopting biometric solutions increasing sharply. This shift allows organizations to strengthen their security posture against identity-related threats while catering to the demand for user-friendly authentication methods
Future Outlook
Over the next five years, the USA Identity and Access Management market is anticipated to experience substantial growth, supported by ongoing advancements in security technologies, heightened awareness of cybersecurity threats, and a growing emphasis on regulatory compliance across industries. The shift towards cloud-based solutions and increased reliance on remote work platforms will further drive demands for innovative IAM solutions.
Major Players
- Microsoft
- IBM
- Okta
- Ping Identity
- CyberArk
- ForgeRock
- SailPoint Technologies
- RSA Security
- Duo Security
- OneLogin
- CA Technologies
- Auth0
- Centrify
- Thales Group
- HID Global
Key Target Audience
- Chief Information Officers (CIOs)
- Information Security Managers
- IT Administrators
- Compliance Officers
- Software Development Teams
- Investments and Venture Capitalist Firms
- Government and Regulatory Bodies (e.g., Department of Homeland Security, National Institute of Standards and Technology)
- System Integrators
Research Methodology
Step 1: Identification of Key Variables
The initial phase involves constructing an ecosystem map encompassing all major stakeholders within the USA Identity and Access Management market. This step is underpinned by extensive desk research, utilizing a combination of secondary and proprietary databases to gather comprehensive industry-level information. The primary objective is to identify and define the critical variables that influence market dynamics.
Step 2: Market Analysis and Construction
In this phase, we will compile and analyze historical data pertaining to the USA Identity and Access Management market. This includes assessing market penetration, the ratio of marketplaces to service providers, and the resultant revenue generation. Furthermore, an evaluation of service quality statistics will be conducted to ensure the reliability and accuracy of the revenue estimates.
Step 3: Hypothesis Validation and Expert Consultation
Market hypotheses will be developed and subsequently validated through computer-assisted telephone interviews (CATIs) with industry experts representing a diverse array of companies. These consultations will provide valuable operational and financial insights directly from industry practitioners, which will be instrumental in refining and corroborating the market data.
Step 4: Research Synthesis and Final Output
The final phase involves direct engagement with multiple Identity and Access Management solution providers to acquire detailed insights into product segments, sales performance, consumer preferences, and other pertinent factors. This interaction will serve to verify and complement the statistics derived from the bottom-up approach, thereby ensuring a comprehensive, accurate, and validated analysis of the USA Identity and Access Management market.
- Executive Summary
- Research Methodology
(Market Definitions and Assumptions, Abbreviations, Market Sizing Approach, Consolidated Research Approach, Understanding Market Potential Through In-Depth Industry Interviews, Primary Research Approach, Limitations and Future Conclusions)
- Definition and Scope
- Market Landscape
- Timeline of Key Developments
- Business Cycle Analysis
- Supply Chain and Value Chain Analysis
- Growth Drivers
Increasing Cybersecurity Threats
Regulatory Compliance Requirements
Growing Adoption of Cloud Services - Market Challenges
High Implementation Costs
Complex Integration with Legacy Systems - Opportunities
Rising Demand for BYOD Policies
Emerging Technologies - Trends
Adoption of AI in IAM
Shift towards Privacy-First Solutions - Government Regulation
Data Protection Laws
Compliance Standards - SWOT Analysis
- Stakeholder Ecosystem
- Porter’s Five Forces
- By Value, 2019-2024
- By Average Pricing, 2019-2024
- By Deployment Type (In Value %)
Cloud
On-Premises
Hybrid - By Solution Type (In Value %)
Multi-Factor Authentication
Single Sign-On
Privileged Access Management
Identity Governance
Access Management - By Industry Vertical (In Value %)
BFSI
IT and Telecom
Healthcare
Government
Retail - By Region (In Value %)
West
Midwest
South
Northeast - By User Type (In Value %)
Individuals
Enterprises
Government Agencies
- Market Share of Major Players on the Basis of Value, 2024
Market Share of Major Players by Type of Identity and Access Management Segment, 2024 - Cross Comparison Parameters (Company Overview, Business Strategies, Recent Developments, Strength, Weakness, Organizational Structure, Revenues, Revenues by Solution Type, Number of Clients, Integration Capabilities, Unique Value offering and others)
- SWOT Analysis of Major Players
- Pricing Analysis Based on Key Solutions Available
- Detailed Profile of Major Players
Microsoft Corporation
IBM Corporation
Okta, Inc.
Ping Identity
Oracle Corporation
CyberArk Software Ltd.
SailPoint Technologies Holdings, Inc.
RSA Security LLC
ForgeRock, Inc.
OneLogin, Inc.
Centrify Corporation
Auth0, Inc.
Duo Security (Cisco)
Thales Group
Hitachi ID Systems
- Market Demand and Utilization
- Budget Allocations
- Regulatory Compliance Considerations
- Needs, Desires, and Pain Point Analysis
- Decision-Making Process
- By Value, 2025-030
- By Average Pricing, 2025-2030


