Market Overview
The Israel Military Cybersecurity market has demonstrated significant growth in recent years, driven by the increasing frequency and sophistication of cyber threats targeting critical national security infrastructure. The market is valued at approximately USD ~billion, with strong demand for advanced cybersecurity solutions across defense agencies, intelligence organizations, and related sectors. This growth is propelled by Israel’s strategic investments in cybersecurity technologies and the government’s commitment to establishing comprehensive defense mechanisms against cyber warfare. As cyberattacks continue to evolve, the market is expected to grow rapidly, driven by heightened security awareness and increasing military expenditure.Israel, with its highly advanced cybersecurity infrastructure, remains a dominant player in the market. Tel Aviv, in particular, serves as a hub for defense and cybersecurity technologies, hosting a large concentration of tech companies and research institutions focused on military cybersecurity. Additionally, the broader Middle East region, due to its political tensions and military activities, has shown heightened interest in strengthening cybersecurity defense systems. Israel’s proactive stance on national security and its strong technological ecosystem contribute to its market dominance in military cybersecurity. 
Market Segmentation
By System Type
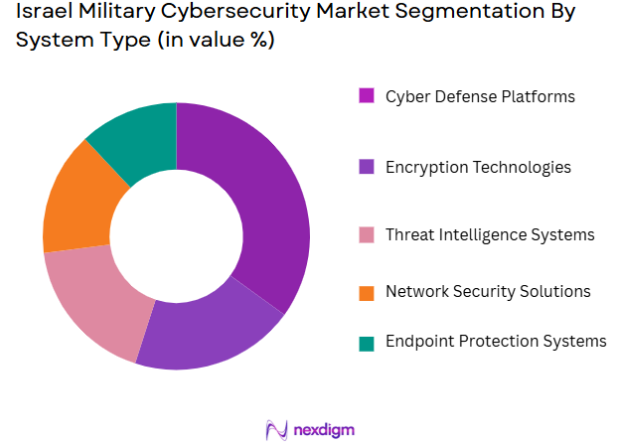
The Israel Military Cybersecurity market is segmented by system type into various categories, such as Cyber Defense Platforms, Encryption Technologies, Threat Intelligence Systems, Network Security Solutions, and Endpoint Protection Systems. Cyber Defense Platforms have the largest market share, driven by their essential role in protecting military networks from cyberattacks. These platforms provide comprehensive security solutions to defend against a wide array of cyber threats, ranging from malware to state-sponsored cyberattacks. Israel’s military forces rely heavily on robust defense mechanisms to secure sensitive data and communication channels. Due to the increasing sophistication of adversaries and the critical nature of national defense networks, the demand for cyber defense platforms remains strong.
By Platform Type
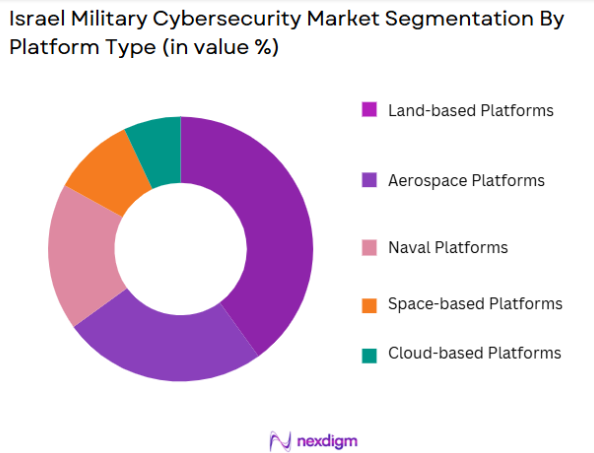
The Israel Military Cybersecurity market is also segmented by platform type, including Land-based Platforms, Aerospace Platforms, Naval Platforms, Space-based Platforms, and Cloud-based Platforms. The largest share is held by Land-based Platforms, as the majority of military cybersecurity operations occur within ground-based defense systems. These platforms typically encompass critical infrastructure such as command centers, military bases, and communication networks, all of which require highly secure environments to function effectively. Land-based military systems are more vulnerable to direct cyberattacks, which is why they account for a larger portion of the cybersecurity market in Israel.
Competitive Landscape
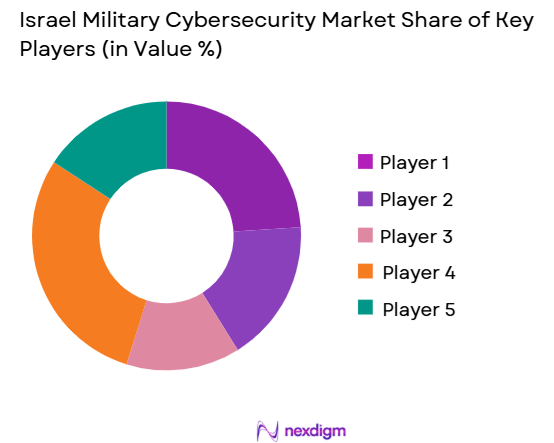
The Israel Military Cybersecurity market is dominated by a few key players, including both local and international companies, with major contributions from Israel-based firms such as Elbit Systems, CyberArk, and Check Point Software Technologies. The industry is highly competitive, with these companies leading the charge in the development of advanced cybersecurity solutions tailored to the unique needs of military defense. Global cybersecurity giants like Palo Alto Networks and Fortinet also maintain a significant presence in the market, offering cutting-edge technologies for national defense agencies.
| Company Name | Establishment Year | Headquarters | Product Focus | R&D Investment | Technological Innovation | Global Presence |
| Elbit Systems | 1966 | Haifa, Israel | ~ | ~ | ~ | ~ |
| CyberArk | 1999 | Petah Tikva, Israel | ~ | ~ | ~ | ~ |
| Check Point Software | 1993 | Tel Aviv, Israel | ~ | ~ | ~ | ~ |
| Palo Alto Networks | 2005 | Santa Clara, USA | ~ | ~ | ~ | ~ |
| Fortinet | 2000 | Sunnyvale, USA | ~ | ~ | ~ | ~ |
Market Analysis
Growth Drivers
Urbanization
Urbanization in Israel has been one of the key growth drivers for the military cybersecurity market. As urban centers continue to expand, the demand for robust cybersecurity solutions to protect critical infrastructure, including government buildings, military bases, and data centers, has intensified. In urban environments, the increased concentration of sensitive data, communication networks, and high-value assets makes these areas attractive targets for cybercriminals and hostile state actors. As more of the population moves into urban areas and digital transformation accelerates, ensuring the security of urban infrastructure becomes a strategic priority. The growth of smart cities, which rely heavily on interconnected systems, further drives the need for sophisticated cybersecurity solutions to protect against potential cyber-attacks that could disrupt urban life. This urban shift necessitates strong defenses against cyber warfare and cybercrime, fueling demand for advanced military cybersecurity technologies tailored to urban needs.
Industrialization
Israel’s rapid industrialization has significantly contributed to the growth of its military cybersecurity market. As industries expand and digitalize, the critical nature of cybersecurity in protecting industrial control systems (ICS) and other operational technologies becomes more evident. Industrialization, particularly in sectors such as defense manufacturing, energy, and transportation, increases the reliance on digital platforms and IoT systems. These systems, if compromised, can disrupt operations, cause financial losses, and endanger national security. Israel’s military cybersecurity solutions are increasingly designed to safeguard industrial infrastructures from cyber-attacks. The expansion of digital industries has led to increased adoption of cybersecurity technologies, focusing on industrial control systems, SCADA systems, and interconnected manufacturing platforms. As Israel continues to innovate and industrialize, ensuring the security of these newly connected and automated systems becomes a key driver for the market.
Restraints
High Initial Costs
One of the primary restraints in the Israel Military Cybersecurity market is the high initial cost associated with advanced cybersecurity systems. Developing, installing, and maintaining cutting-edge cybersecurity solutions requires substantial investment, particularly for military agencies that require customized, high-security solutions to defend critical infrastructure. The cost of adopting new technologies, training personnel, and ongoing system updates can place significant financial strain on defense budgets. Additionally, the cost of integrating cybersecurity measures across various military platforms, such as land, aerospace, and naval systems, adds further complexity. Although the long-term benefits in terms of security and protection of national assets are substantial, the initial capital expenditure required can deter smaller entities or governments with limited financial resources. This financial burden limits the adoption of high-end cybersecurity solutions, particularly in emerging markets or regions with constrained defense budgets.
Technical Challenges
The Israel Military Cybersecurity market also faces significant technical challenges that hinder the development and deployment of security systems. As cyber threats become more sophisticated, military cybersecurity technologies must evolve quickly to stay ahead of new vulnerabilities and attack vectors. However, this rapid pace of change can lead to integration difficulties, particularly in legacy military systems that were not designed to be compatible with modern cybersecurity protocols. Additionally, the increasing complexity of cyber-attacks requires military agencies to continually update and adapt their systems, which can be technically challenging. Ensuring interoperability between various defense platforms, securing communication channels, and maintaining the effectiveness of cybersecurity defenses across multiple layers of military operations require highly specialized knowledge. Moreover, skilled cybersecurity professionals who can manage and address these challenges are in short supply, further complicating the issue. This ongoing technological evolution and skill gap present significant obstacles for the market.
Opportunities
Technological Advancements
Technological advancements present significant opportunities for the Israel Military Cybersecurity market. Innovations in artificial intelligence (AI), machine learning (ML), and blockchain technology are opening new doors for improving military cybersecurity defenses. AI and ML can be utilized to develop predictive threat detection systems that analyze vast amounts of data in real-time to identify patterns and detect anomalies before they turn into security breaches. Furthermore, blockchain technology can enhance data integrity and secure communications, making it a valuable tool for military cybersecurity. These technologies not only strengthen existing systems but also allow for the development of new, more efficient security frameworks capable of adapting to evolving threats. As cybersecurity technologies continue to advance, Israel’s military cybersecurity industry stands to benefit from cutting-edge solutions that can offer higher security, efficiency, and protection across all defense platforms.
International Collaborations
International collaborations represent a significant opportunity for the Israel Military Cybersecurity market. As global cyber threats become increasingly sophisticated, countries around the world are seeking to strengthen their cybersecurity capabilities through alliances and shared knowledge. Israel, with its advanced cybersecurity infrastructure and expertise, is positioned as a key player in global defense collaborations. These partnerships allow for the exchange of intelligence, joint research, and development of new cybersecurity technologies. Additionally, Israel’s participation in international defense agreements and its role in NATO cybersecurity initiatives can drive the adoption of its military cybersecurity solutions worldwide. Collaborations also enable the sharing of best practices and the standardization of cybersecurity protocols, improving overall defense capabilities across multiple nations. Through these international partnerships, Israel can expand its market reach and influence, providing advanced military cybersecurity solutions to a broader audience while strengthening global defense networks.
Future Outlook
Over the next decade, the Israel Military Cybersecurity market is expected to continue its robust growth, driven by advancements in AI and machine learning technologies, as well as increasing government investment in defense and cybersecurity sectors. With the growing complexity of cyberattacks and emerging cyber threats, the Israeli defense industry is likely to see heightened demand for innovative solutions to protect its national security assets. The military’s reliance on digital and networked systems will also fuel the need for comprehensive cybersecurity strategies, making this sector an essential pillar of national defense.
Major Players
- Elbit Systems
- CyberArk
- Check Point Software
- Palo Alto Networks
- Fortinet
- Radware
- Raytheon Technologies
- Israel Aerospace Industries
- NICE Systems
- McAfee
- Tanium
- Sophos
- Verint Systems
- FireEye
- CrowdStrike
Key Target Audience
- Investments and venture capitalist firms
- Government and regulatory bodies
- Military organizations
- Intelligence agencies
- Defense contractors
- National cybersecurity authorities
- Technology integrators in defense sector
- Armed forces and security agencies
Research Methodology
Step 1: Identification of Key Variables
The initial phase involves identifying the key stakeholders and variables within the Israel Military Cybersecurity Market. This will include reviewing secondary data sources, industry reports, and conducting interviews with key experts to establish the parameters driving market growth.
Step 2: Market Analysis and Construction
This phase will focus on gathering historical data related to market trends, defense spending, and technological adoption within the cybersecurity domain. The analysis will include assessing the market dynamics such as the scale of cyberattacks, governmental cybersecurity initiatives, and their impact on the defense sector.
Step 3: Hypothesis Validation and Expert Consultation
After forming hypotheses, the next phase involves validating them through primary research, including interviews and consultations with industry professionals, such as cybersecurity experts and military officers, to obtain qualitative insights and validate the market assumptions.
Step 4: Research Synthesis and Final Output
The final phase will involve synthesizing the data gathered from primary and secondary sources, followed by a comprehensive analysis of the market. The final report will be consolidated with a detailed look at the competitive landscape, market segmentation, and key players operating within the market.
- Executive Summary
- Research Methodology(Definitions, Scope, Industry Assumptions, Market Sizing Approach, Primary & Secondary Research Framework, Data Collection & Verification Protocol, Analytic Models & Forecast Methodology, Limitations & Research Validity Checks)
- Market Definition and Scope
- Value Chain & Stakeholder Ecosystem
- Regulatory / Certification Landscape
- Sector Dynamics Affecting Demand
- Strategic Initiatives & Infrastructure Growth
- Growth Drivers
Rising cybersecurity threats and attacks
Government initiatives for cybersecurity enhancement
Increased investment in defense sector modernization - Market Challenges
Evolving and sophisticated cyber threats
High costs associated with advanced cybersecurity systems
Lack of skilled cybersecurity professionals - Trends
Integration of AI-driven cybersecurity systems
Shift towards cloud-based military cybersecurity solutions
Increased adoption of zero-trust architecture
- Market Opportunities
Emerging technologies like AI and machine learning in cybersecurity
Partnerships between government and private sector for cybersecurity solutions
Expansion of cybersecurity infrastructure for critical national assets
- Government regulations
Mandatory cybersecurity standards for defense contractors
National defense and security-related cybersecurity policies
Cybersecurity compliance for critical infrastructure - SWOT analysis
Strengths: Leading global cybersecurity expertise in Israel
Weaknesses: Dependence on high-cost technologies
Opportunities: Increasing demand for cybersecurity in national defense systems - Porters 5 forces
Threat of new entrants: Moderate
Bargaining power of suppliers: High
Bargaining power of buyers: Moderate
Threat of substitutes: Low
Industry rivalry: High
- By Market Value, 2020-2025
- By Installed Units, 2020-2025
- By Average System Price, 2020-2025
- By System Complexity Tier, 2020-2025
- By System Type (In Value%)
Cyber defense platforms
Encryption technologies
Threat intelligence systems
Network security solutions
Endpoint protection systems - By Platform Type (In Value%)
Land-based platforms
Aerospace platforms
Naval platforms
Space-based platforms
Cloud-based platforms - By Fitment Type (In Value%)
Hardware-based solutions
Software-based solutions
Integrated solutions
Cloud-native security solutions
Hybrid systems - By EndUser Segment (In Value%)
Defense forces
Intelligence agencies
Cyber defense contractors
Critical infrastructure sectors
Government entities - By Procurement Channel (In Value%)
Direct procurement
Third-party procurement
Through defense contractors
Government procurement tenders
Private sector procurement
- Market Share Analysis
- CrossComparison Parameters(Market share by company, technological innovations, geographic reach, customer base, pricing strategies)
- SWOT Analysis of Key Competitors
- Pricing & Procurement Analysis
- Key Players
Check Point Software Technologies
Israel Aerospace Industries
Elbit Systems
Radware
Verint Systems
NICE Systems
CyberArk
Tanium
Sophos
McAfee
Fortinet
Palo Alto Networks
CrowdStrike
Raytheon Technologies
Northrop Grumman
- Defense forces require advanced cybersecurity solutions for military operations
- Intelligence agencies focus on real-time threat intelligence
- Cyber defense contractors collaborate with military forces to enhance security
- Critical infrastructure sectors demand cybersecurity solutions for safety
- Forecast Market Value, 2026-2035
- Forecast Installed Units, 2026-2035
- Price Forecast by System Tier, 2026-2035
- Future Demand by Platform, 2026-2035