Market Overview
The KSA Military Cybersecurity market is valued at USD ~billion based on a comprehensive analysis of historical data. The growth of this market is propelled by a combination of increasing cyber threats targeting national security, and the Saudi Arabian government’s significant investments in cybersecurity infrastructure. As the country accelerates its digital transformation, military defense and cybersecurity solutions have become essential for safeguarding critical national assets. With national security at stake, the need for robust cybersecurity solutions in the military sector continues to rise, establishing a steady demand for advanced defense mechanisms.
The dominant countries in the KSA Military Cybersecurity market are Saudi Arabia, the UAE, and Qatar. Saudi Arabia, being the largest player, leads the market due to its substantial investments in defense and cybersecurity, focusing on securing national assets, military data, and critical infrastructure. The UAE’s strategic geographic location and defense alliances make it another key player, with increasing collaboration in cybersecurity solutions. Qatar also contributes to the regional dominance through its modernization of military infrastructure, prioritizing cybersecurity as a critical aspect of its national defense strategy.
Market Segmentation
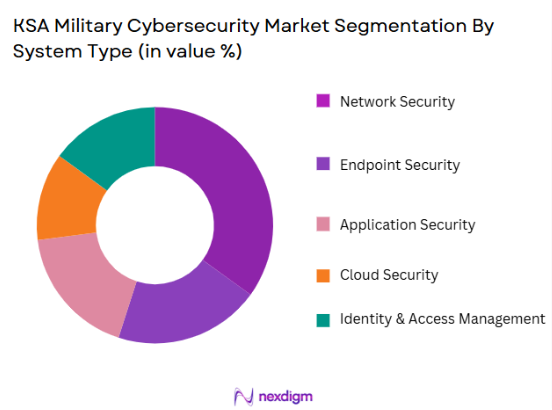
By System Type
The KSA Military Cybersecurity market is segmented by system type into network security, endpoint security, application security, cloud security, and identity & access management. The network security segment is currently the dominant sub-segment due to the growing need for robust protection of defense networks from external cyber-attacks. Military and defense networks are increasingly targeted by cyber threats, making network security solutions a priority. With the advancement of technologies like AI and machine learning, network security has become an essential layer in safeguarding military communications and operations, contributing to its market leadership in this segment.
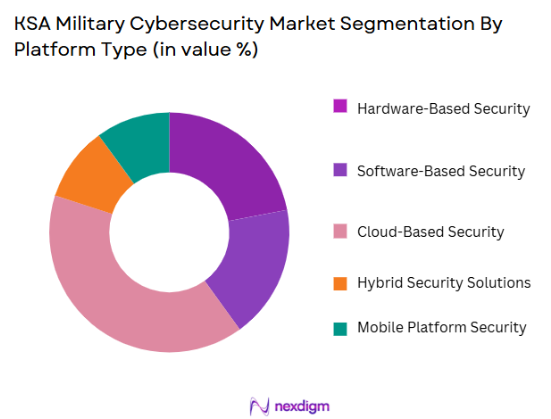
By Platform Type
The KSA Military Cybersecurity market is segmented by platform type into hardware-based security, software-based security, cloud-based security, hybrid security solutions, and mobile platform security. Cloud-based security dominates this segment as more military agencies are adopting cloud computing solutions for data storage and operational scalability. The shift toward cloud environments requires robust cloud security frameworks, which ensure secure data handling and minimize the risk of breaches. The rapid transition to cloud infrastructure within military operations is the primary factor for the increasing demand for cloud-based security systems in the market.
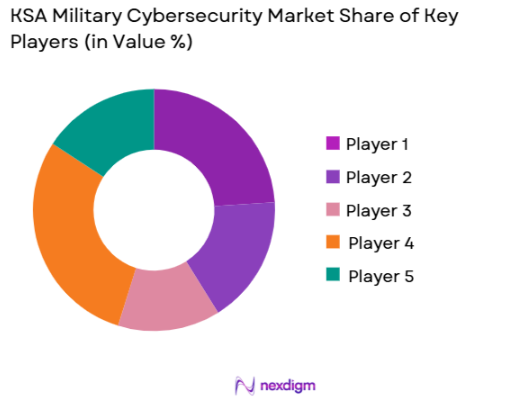
Competitive Landscape
The KSA Military Cybersecurity market is primarily dominated by several major players, including global defense and cybersecurity giants such as Raytheon Technologies, Thales Group, and BAE Systems, along with regional leaders like Saudi Arabian Military Industries (SAMI). These companies play a vital role in ensuring the cybersecurity of national defense systems by providing state-of-the-art solutions. The collaboration between local and international players strengthens the market, highlighting the key role these companies play in the region’s cybersecurity efforts.
| Company | Establishment Year | Headquarters | Technology Focus | Key Products | Regional Presence | Strategic Alliances |
| Raytheon Technologies | 1922 | Waltham, USA | ~ | ~ | ~ | ~ |
| Thales Group | 2000 | Paris, France | ~ | ~ | ~ | ~ |
| BAE Systems | 1999 | London, UK | ~ | ~ | ~ | ~ |
| Saudi Arabian Military Industries (SAMI) | 2017 | Riyadh, Saudi Arabia | ~ | ~ | ~ | ~ |
| Lockheed Martin | 1995 | Bethesda, USA | ~ | ~ | ~ | ~ |
Market Analysis
Growth Drivers
Urbanization
Urbanization in Saudi Arabia is rapidly transforming the country’s infrastructure, including the military and defense sectors. As cities expand and digital transformation accelerates, the need for robust cybersecurity solutions becomes even more critical. The integration of smart city concepts, IoT devices, and AI technologies within urban centers leads to increased exposure to cyber threats. As urban areas become hubs of activity and innovation, protecting the data and critical infrastructure becomes a top priority for the military. The growing urban population also drives the demand for cybersecurity solutions that protect both public and military assets, from transportation networks to communication systems. As Saudi Arabia continues to modernize its military capabilities in alignment with its Vision 2030 objectives, urbanization is a key factor fueling the demand for more advanced and scalable cybersecurity solutions tailored to a complex, interconnected environment.
Industrialization
The industrialization of Saudi Arabia plays a significant role in the growing demand for military cybersecurity solutions. As industries such as oil and gas, manufacturing, and defense technologies become more digitized, the need to protect critical infrastructure becomes more pronounced. Industrial systems and manufacturing processes are increasingly connected to digital networks, creating new vulnerabilities for cyber threats. The Saudi military is directly involved in securing the industrial base, particularly critical industries like oil and gas, which are vulnerable to cyberattacks that could have national security implications. The government’s drive for increased industrial capacity and defense integration means that the military must protect its infrastructure and technologies from cyberattacks. Industrialization thus accelerates the demand for advanced cybersecurity systems to safeguard both private and public sector critical infrastructure, ensuring national security and economic stability.
Restraints
High Initial Costs
The high initial costs associated with implementing advanced cybersecurity systems pose a significant barrier to growth in the KSA military cybersecurity market. Advanced cybersecurity solutions, such as AI-driven defense systems, require significant investment in both hardware and software, which can be a challenge for the military budget. The upfront costs involved in acquiring, integrating, and maintaining these systems can be prohibitive for some defense agencies, particularly when they need to upgrade existing infrastructure to meet new cybersecurity demands. While long-term benefits such as enhanced security and reduced risks are clear, the financial burden of acquiring these solutions may limit the pace of adoption. Moreover, there is a need for specialized personnel and training, further adding to the overall expenditure. The high initial costs may cause delays in the widespread implementation of state-of-the-art military cybersecurity solutions, particularly in less wealthy regions of the country.
Technical Challenges
Technical challenges also serve as a restraint for the expansion of the KSA military cybersecurity market. As the military embraces new technologies like AI, blockchain, and cloud computing, integrating these complex systems with existing infrastructure often leads to compatibility issues and operational difficulties. Additionally, the fast-paced evolution of cyber threats requires that military systems be consistently updated and adapted, placing pressure on the cybersecurity industry to continuously innovate. The complexity of maintaining cutting-edge cybersecurity solutions, along with the integration of new technologies into existing defense frameworks, presents significant technical challenges. Moreover, ensuring the interoperability of these systems across various platforms and services within the military can prove difficult. These technical barriers hinder the seamless adoption and deployment of cybersecurity technologies, potentially delaying the ability to counter new and sophisticated cyber threats.
Opportunities
Technological Advancements
Technological advancements present significant opportunities for the growth of the KSA military cybersecurity market. The integration of emerging technologies such as artificial intelligence (AI), machine learning (ML), and blockchain within cybersecurity systems has the potential to revolutionize military defense strategies. AI-driven solutions can enhance real-time threat detection, enabling faster responses to cyberattacks and more proactive defense measures. Machine learning can further improve the accuracy of cybersecurity systems by adapting to evolving threats without requiring manual updates. Additionally, blockchain technology can provide robust encryption and decentralized security systems, offering an additional layer of protection against cyberattacks. As the Saudi military continues to modernize and incorporate these technologies, the demand for advanced cybersecurity solutions will increase. These advancements offer military organizations the opportunity to enhance their cybersecurity defenses, making them more resilient against complex and persistent cyber threats. The implementation of cutting-edge technologies is essential for maintaining national security in an increasingly digital world.
International Collaborations
International collaborations present a significant opportunity for the growth of the KSA military cybersecurity market. Saudi Arabia’s strategic partnerships with global powers, such as the United States and the European Union, in defense and cybersecurity areas enhance its capabilities to counter cyber threats. Through these collaborations, Saudi Arabia gains access to cutting-edge cybersecurity technologies, advanced threat intelligence, and expertise from some of the world’s leading cybersecurity providers. These partnerships enable the country to bolster its defense infrastructure and improve national cybersecurity strategies. Additionally, international collaborations allow for the sharing of best practices and the development of joint defense initiatives that focus on tackling common cyber threats. By strengthening its ties with key international players, Saudi Arabia can enhance its military cybersecurity resilience, benefiting from a wider pool of resources and knowledge. These global alliances help position the KSA military as a formidable force in the region’s cybersecurity landscape.
Future Outlook
Over the next decade, the KSA Military Cybersecurity market is expected to continue its robust growth trajectory, driven by the Kingdom’s expanding defense sector and increasing investments in digital security infrastructure. The evolution of cybersecurity solutions will align with the military’s focus on modernizing its defense strategies and ensuring the protection of national data and military networks. With the ongoing development of cybersecurity technologies and the growing sophistication of cyber threats, the market is positioned for significant growth.
Major Players in the Market
- Raytheon Technologies
- Thales Group
- BAE Systems
- Saudi Arabian Military Industries
- Lockheed Martin
- Northrop Grumman
- General Dynamics
- L3Harris Technologies
- Leidos
- Cisco Systems
- IBM
- Atos
- Palo Alto Networks
- McAfee
- Accenture
Key Target Audience
- Investments and Venture Capitalist Firms
- Ministry of Defense
- Royal Saudi Air Force
- Saudi Arabian National Guard
- Saudi Arabian Army
- Saudi Communications and Information Technology Commission
- Security Agencies
- Private Defense Contractors
Research Methodology
Step 1: Identification of Key Variables
In this initial phase, we conducted extensive desk research to map out all relevant variables influencing the KSA Military Cybersecurity market. This involved analyzing key drivers such as government cybersecurity initiatives, technological advancements, and regional defense strategies, using both secondary sources and proprietary data.
Step 2: Market Analysis and Construction
We compiled and analyzed historical data on the KSA Military Cybersecurity market, evaluating revenue, market size, and market penetration. Detailed insights were gathered regarding various system types, platform types, and industry trends to create a comprehensive market construction for the period under study.
Step 3: Hypothesis Validation and Expert Consultation
Market hypotheses were validated through direct consultations with industry experts and key players in the cybersecurity and defense sectors. These consultations helped refine our understanding of market dynamics, ensuring the credibility of the data and predictions.
Step 4: Research Synthesis and Final Output
The final output was synthesized by engaging with manufacturers, suppliers, and military agencies to validate key findings and hypotheses. This phase ensured that the insights and forecast were accurate, providing an in-depth analysis of the KSA Military Cybersecurity market.
- Executive Summary
- Research Methodology(Definitions, Scope, Industry Assumptions, Market Sizing Approach, Primary & Secondary Research Framework, Data Collection & Verification Protocol, Analytic Models & Forecast Methodology, Limitations & Research Validity Checks)
- Market Definition and Scope
- Value Chain & Stakeholder Ecosystem
- Regulatory / Certification Landscape
- Sector Dynamics Affecting Demand
- Strategic Initiatives & Infrastructure Growth
- Growth Drivers
Increase in Cyber Threats to National Security
Government Investment in Cyber Defense Infrastructure
Advancements in AI and Machine Learning for Cybersecurity - Market Challenges
High Cost of Advanced Cybersecurity Solutions
Limited Skilled Workforce in Cybersecurity
Challenges in Ensuring Real-Time Security and Threat Response - Market Opportunities
Increasing Cybersecurity Collaboration with Global Defense Networks
Growth of Defense Industry in the Middle East
Emerging Demand for Advanced Encryption Technologies - Trends
Rise of AI-Driven Cybersecurity Solutions
Increased Investment in Military Cybersecurity Infrastructure
Adoption of Blockchain Technology for Enhanced Security - Government regulations
Regulations on Cybersecurity Compliance for Military Systems
Mandatory Cybersecurity Certifications for Military Equipment
Cyber Defense Laws to Ensure National Security - SWOT analysis
Strength: Increasing Government Focus on Cybersecurity
Weakness: High Dependency on Foreign Technology Providers
Opportunity: Expansion of Cybersecurity Solutions for Smart Military Systems - Porters 5 forces
Threat of New Entrants: Moderate due to High Capital Requirements
Bargaining Power of Suppliers: High due to Specialized Solutions
Threat of Substitutes: Low due to Specialized Nature of Solutions
- By Market Value, 2020-2025
- By Installed Units, 2020-2025
- By Average System Price, 2020-2025
- By System Complexity Tier, 2020-2025
- By System Type (In Value%)
Network Security
Endpoint Security
Application Security
Cloud Security
Identity & Access Management - By Platform Type (In Value%)
Hardware-Based Security
Software-Based Security
Cloud-Based Security
Hybrid Security Solutions
Mobile Platform Security
- By Fitment Type (In Value%)
On-Premise Deployment
Cloud Deployment
Hybrid Deployment
Edge Security Solutions
Integrated Security Systems - By EndUser Segment (In Value%)
Military & Defense Agencies
Government Institutions
Private Defense Contractors
Intelligence Agencies
Critical Infrastructure Operators - By Procurement Channel (In Value%)
Direct Procurement from Manufacturers
Procurement via Third-Party Integrators
Government Tenders & Contracts
Private Sector Deals
International Collaboration
- Market Share Analysis
- CrossComparison Parameters(Market Share, Revenue Growth, Technological Advancements, Product Innovation, Geographic Presence)
- SWOT Analysis of Key Competitors
- Pricing & Procurement Analysis
- Key Players
Raytheon Technologies
Thales Group
BAE Systems
Northrop Grumman
Lockheed Martin
General Dynamics
L3Harris Technologies
IBM
Atos
Leidos
Cisco
Hewlett Packard Enterprise
Accenture
McAfee
Palo Alto Networks
- Increased Demand for Integrated Cybersecurity Solutions in Military
- Government Focus on Protecting National Defense Networks
- Adoption of Advanced Cybersecurity for Critical Military Infrastructure
- Growing Need for Cybersecurity in Autonomous Military Systems
- Forecast Market Value, 2026-2035
- Forecast Installed Units, 2026-2035
- Price Forecast by System Tier, 2026-2035
- Future Demand by Platform, 2026-2035